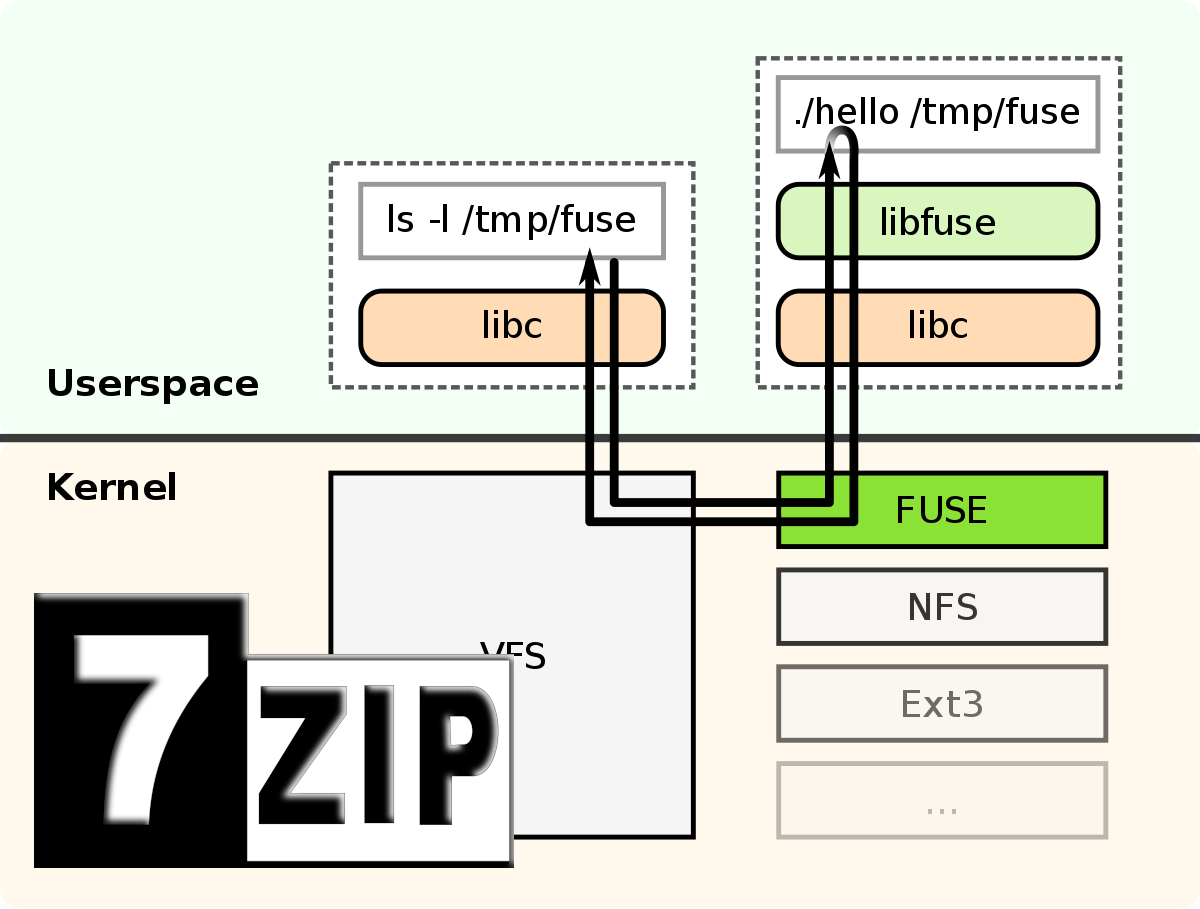
Work in progress As many of you, I also have Windows 10 natively on my Notebook and don't want to switch to Linux, every time, I do some development that…
Pushing the Rectangle Through the Round – Develop With RIOT OS on Windows – Doing The Impossible